IP Ports
This article describes ports, how they are used, and how they work.
Ports were developed so that network devices and computers could accept data from multiple sources over the same IP address. Here is a simple example. Your TV service is the Internet, and the ports are your channels. You have many forms of entertainment, news, and information available through many different channels. Lets say 9xM is channel 85 on your TV. The same is true for web servers that run on port 80. Every port has a special purpose just as each channel serves a different television program. While you only have 1 cable TV subscription, you can still receive multiple channels.
Two main types of ports: TCP and UDP. TCP stands for Transmission Control Protocol. UDP stands for User Data Protocol. Some programs on your computer will use TCP ports to communication and other may use UDP. It is important to know the difference between how the two operation. See TCP vs. UDP for an illustrated example.
There are 65,535 TCP and UDP ports available to transmit data with. Ports 0-1023 are reserved for common use. These ports are assigned by the IANA (Internet Assigned Numbering Authority). This means, that every port from 0-1023 will be the same on every system. For example, let's say a server in New York is using port 80, and so is a server Texas. Because port 80 falls in the range of reserved ports, we know both servers are using port 80 for HTTP connections. Viewing a list of known ports can help you determine which type of connections are present on your machine.
Computer or network devices often "listen" on certain ports. For example, a server running web, FTP, and Telnet services will listen on a port for each. Port 80 for web, 21 for FTP, and 23 for telnet. The act of listening simply means the machine is waiting for another device to connect to it. See the illustration below:
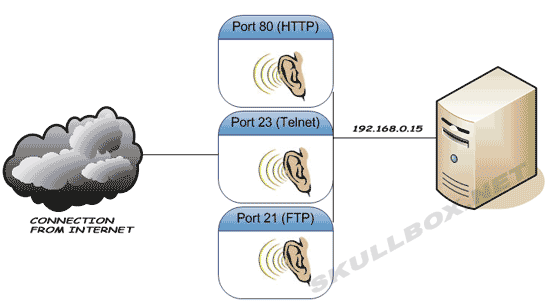
Notice that the server is listening for 3 ports over a single IP address (192.168.0.15). It is possible for multiple devices to connect to a single port. Meaning, a telnet server may accept over 100 simultaneous connections to port 23. Once a connection is established it is know as a "session."
Comments
Post a Comment